Interactive Login with SSH, Security and different Clients
Contents
Motivation
Direct, interactive login is the easiest way to connect to a remote server. The tool we learn here is SSH which stands for Secure SHell
. You will learn what kind of clients are available and what the kind of security SSH even offers.
Interactive Login with SSH
If you have an account on a Linux server and the Linux sever offers SSH access you can login with, e.g.:
$ ssh anna@testbox.example.org
This assumes the username on the remote machine is anna and the remote server has a name testbox.example.org
The authenticity of host 'testbox.example.org (47.11.8.15)' can't be established. ECDSA key fingerprint is SHA256:lfhcdopeCQcFKHjjek3522903dd. Are you sure you want to continue connecting (yes/no)?
The first time you connect it will ask you if you trust this machine and will show a cryptographic fingerprint of the public key that the remote machine uses. That fingerprint is stored in a file .ssh/known_hosts and the next time you connect it will know that it is the same machine. If you do not have a host name you can also use the IP address.
If the username on your local machine is the same as on the remote machine, in the case above: anna, then you can omit the username part.
If you do not have a remote maschine you could, for this example also ssh into the same machine where you are currently working. The IP address will be 127.0.0.1 or you could use localhost as your hostname.
Copy Files via SSH
One nice thing is that you an also use SSH to copy files. This way you do not need any file-sharing protocols, which would be troublesome over internet connections anyways.
You can either use scp (secure copy) or sftp. Here are some scp examples:
$ scp img001.jpg anna@example.org: #copy image file into home directory
$ scp -r Pictures/ anna@example.org:/var/mywebsite/ # recusive copy of everything in
# Picutres to a remote folder
$ scp anna@example.org:/etc/hostname . # copy that file into current directory .
Note the format: user@host:directory-or-filename
After the : is the place where you specify the remote file. If nothing is there it is your home directory. Also note: When you want to copy something to your home directory to use the dot. -r is used for recursive
- to copy a whole tree.
What kind of Security does SSH offer?
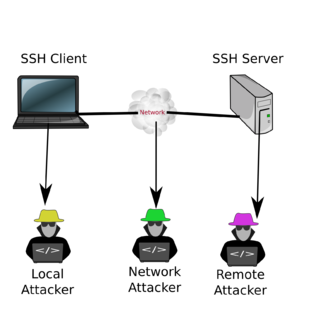
The first S in SSH stands for secure. But what kind of protections does SSH offer? The S means that the connection to your server is encrypted. This means that someone on the network can not spy on you. The identity of the remote machines is also checked with the fingerprint of they key that was used on the first connection. This prevents man-in-the-middle attacks. The only real danger here is the first connection: If you do not know the fingerprint of the remote machine then an attacker could hijack the connection at the first attempt. You could protect yourself by distributing the fingerprints beforehand. Newer versions of ssh also allow for signed keys, but this is rarely used.
Of course, the SSH does not protect you against a local attacker. If the machine that you use is already compromised, an attacker can read all your keystrokes and see all the output from the remote machine. So you should not login form a public internet cafe or any other insecure machine.
The most sensible type of information that could be stolen, of course is your password. In a normal, interactive login with password, the passwords is typed in on your machine, then encrypted and de-crypted on the remote end, where the hash function is used to compare it to the hashed password in the /etc/shadow. This means, an attacker that has taken over the remote machine could have installed a compromised version of the sshd and read your passwords in plain!
You can use password-less login with public-key login to avoid this issue, but still if you use password based login then you should really have a different password on all the machines you use! Otherwise an attacker could use this to also compromise all other machines where you have login.
SSH Clients
On Linux and Mac you have the standard ssh client, but you can also use connect to SSH from almost any system. Of course the danger is that mobile phones are not very secure...
| Linux, Mac | ssh | default ssh command line client |
| Windows | Putty | putty is a free software client: https://www.chiark.greenend.org.uk/~sgtatham/putty/ |
| Android | ConnectBot | Free software, From AppStore |
| iPhone | Terminus, Shelly, Blink Shell,... | I think all of them are commercial |
File transfer is supported by many graphical tools. WinSCP, ... In Linux Gnome or KDE you can press Ctrl-L in the filemanager and enter a URL: sftp://user@hostname to connect and copy files.
Exercises
- Try to find a system where you can login with ssh.
- Try to copy files to and from the system using scp or sftp
- Think about: Who could have intercepted the passwords when you logged in?