Firewall Basics
Contents
Motivation
Protecting your Linux from threats on the Internet is ever more important today. For this you should turn off any service that you do not need and also keep your distribution up to date. A firewall also helps to prevent unwanted guests. Using Linux as a firewall to protect your network is also often a good idea. Last but not least: The NAT (Network Address Translation) built into the Linux firewall code is useful if you want a private network behind a Linux router.
The History of the Linux Firewall, replacing iptables with nftables
In the 1990, even before Linux, there was TCP Wrappers which could be used to protect a server program from access by using a list of IP addressed that would be allowed or denied access to a server. It is still in use today, thought most firewall rules are now handled by the kernel:
The Linux had firewalling code in the kernel since about 1997. Back then it was ipfwadm. With the 2.2 kernels came ipchains. This was then replaced with the iptables firewall. iptables was the Linux firewall for the last 20 years. Modern distributions are now replacing this with the netfilter
or nftables firewall.
In order to set up rules or display the existing rules there are tools that talk to the kernel interface. For iptables the tools was iptables
. For the modern nftables the tools is nft
.
Current kernels have an iptables-compatibilty layer, so even if they run nftables internally, a firewall can still be configured (for the most part) with the old iptables commands.
In order to make the transition towards the new nft rules easier there is a tool named iptables-translate, that has the same syntax as iptables but does not insert any firewall rules into the kernel, instead it prints out which nft command would do the trick. So if you find a documentation that tells you about an iptables command then you can use the tool to find the way to do it in nft.
nft allows more freedom in how you structure your firewalls, but since it is rather new most Linux firewalls, even when they use nft, will follow the iptables structure. Thus I first give you a short overview of iptables:
iptables overview
iptables has 3 main tables where you can put firewall rules.
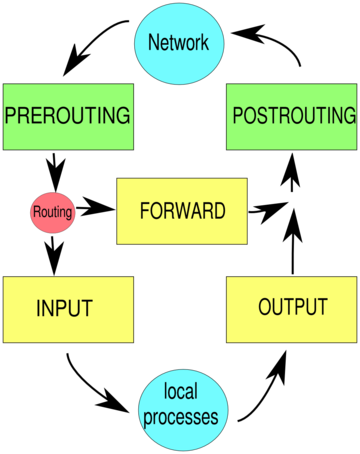
- INPUT chain
- Where all packets are filtered that should be processed by local services
- OUTPUT chain
- Where you can filter packets that were generated locally on your computer
- FORWADING chain
- This can be used to filter all packets which are forwarded from on interface to another one. This table is only used when packet forwarding is enabled - that is when you are using your computer as a router.
Then there are the to NAT tables
. These are only used for network translation. If you want to dynamically rewrite package addressed. E.g. to use your private addresses behind a real IP address. In the iptables too you have to use the option -t nat to see them or use them.
The following commands would list all rules in the normal tables and the nat tables:
# iptables -L # iptables -L -t nat
The option -F cold be used to flush (clear) all rules in that set of tables.
filtering incoming packets with iptables
Here are is a simple examples of using IP tables:
# iptables -I INPUT -j DROP -i eth1 -p tcp --dport 22 -s 0/0 # iptables -I INPUT -j ACCEPT -s 182.16.21.0/24 -p tcp --dport 22
Here is what that does: the -I option inserts the rule on top of the chain (it thus has precedence over all other rules that might be in the chain already. (-A would append at the end of the table). -j tells the target of the rule. The target can be another table (e.g. one that you created yourself). Here we directly say we want to DROP certain packages and ACCEPT others. Once you come to a DROP or ACCEPT rule the processing is finished and the packets will be dropped or it will pass. The first rule above will drop all TCP packets that go to port 22 (SSH) if they come from the network card eth1. The second rule will allow ssh packets if they come from the 182.16.21.0/24 network. Since the 2nd rule will end up being the first in the chain it has precedence over the drop rule.
simple nat with iptables
# iptables -t nat -I POSTROUTING -j SNAT -s 10.0.0.0/8 --to-source 123.231.12.222
The above rule will create a NAT processing for all packets that come from a source in the 10.x.x.x network. It will rewrite the source of outgoing packets to the 123.231.12.222 IP address. (It only makes sense to use an IP address that is a local address of that computer. Otherwise return packets would never reach you). You do not need another rule for the return packets: the NAT code keeps track of all open connections and transparently rewrites the return packets to go to the original sender.
nftables overview
The translation of the above example rules to the netfilter tables
would be:
# nft insert rule ip filter INPUT iifname "eth1" tcp dport 22 counter drop # nft insert rule ip filter INPUT ip saddr 182.16.21.0/24 tcp dport 22 counter accept
and for the SNAT example
# nft insert rule ip nat POSTROUTING ip saddr 10.0.0.0/8 counter snat to 123.231.12.222
As the nftables have no need for those tables used in iptables, the above example assume that there are tables defined to match the functionality of the old iptables. In the netfilter that chains can have any name but to get packets to that chain you they must come from one of the so called netfilter hooks.
The hooks
correspond to the names of the chains we have seen above for the iptables.
To list all current rules. Below you see an empty set of rules that corresponds to an empty iptables firewall:
# nft list ruleset -a
table ip filter { # handle 4
chain INPUT { # handle 1
type filter hook input priority 0; policy accept;
}
chain FORWARD { # handle 2
type filter hook forward priority 0; policy accept;
}
chain OUTPUT { # handle 3
type filter hook output priority 0; policy accept;
}
}
table ip nat { # handle 5
chain PREROUTING { # handle 1
type nat hook prerouting priority -100; policy accept;
}
chain INPUT { # handle 2
type nat hook input priority 100; policy accept;
}
chain POSTROUTING { # handle 3
type nat hook postrouting priority 100; policy accept;
}
chain OUTPUT { # handle 4
type nat hook output priority -100; policy accept;
}
}
For more detailed information here is the link to the nftables wiki and the nft cheet sheet
What else can you do with firewalls?
- Counting and logging certain types of packets. Useful e.g. for intrusion dedection.
- Redirecting incoming packtes (DNAT). They can also be directed to local servers.
- Filtering arp and bridge traffic.
Exercises
- Look at your Linux system and see if there are any firewall rules instead? Is nft already avaliable?
- Build some rules to filter incoming packets to some server port. See if you can still reach it from outside. Try to include a counter in your rule and see when the counter counts up. (You can see the counter when you display the rules).
- Build some rules to filter outgoing traffic to some server. Also add some counter again.