Network Tools in Linux
Contents
Motivation
We have learned the basics of how a network works. Now lets look at more tools that help you debug and troubleshoot network issues.
DNS Lookup
When you go to a website you do not need to remember the IP address. You use a name for that. e.g. you go to www.google.com. In order to find the associated IP address you need to lookup that name. The tools for that are: host nslookup or dig. For simple lookups I prefer host, while the other tools will give you more detailed information of how the lookup worked.
host www.google.com www.google.com has address 172.217.16.196 www.google.com has IPv6 address 2a00:1450:4001:817::2004
Sometimes you want to define aliases for certain hosts. Especially in your private network at home you will not want to run your own DNS system. A simple file that relates IP addresses to names will be sufficient to make your life easiser. This is the /etc/hosts file where you can add names to your IP addresses. E.g. your hosts file could look like this:
$ cat /etc/hosts 127.0.0.1 localhost ::1 localhost ip6-localhost ip6-loopback 192.168.19.27 laptop1 acer 192.168.19.101 handy lg200 192.168.19.1 netgear
In this example we have defined 3 names in the 192.168.19.0/24 network. You can add alias names after the first name. It is also good to have the name of your own computer defined. Also the loopback interface should be named localhost
. In the above example we also name the IPv6 address (::1) to be localhost.
ping
Ping is a tool that sends out a special packet (ICMP Echo) to another station and receives the answer from the other side. This is useful to see if the other station is alive or if the network connection to the other side is working. Of course the other side could choose to not answer the packet or there could be a firewall in between us and the remote side that filter either request packet or the response.
Ping comes from sonar, where a short sound is sent out (a Ping
) and the echo is used to find out if there is an object ahead and how far it is away. The network ping also measures the time that it takes for the response.
You can tell the ping tool how many packets it sends, in which interval and what the size of the packets should be. On Linux the default number of packets is infinity. So you need to interrupt the tool by pressing Ctrl-C.
$ ping www.google.com PING www.google.com (172.217.16.196) 56(84) bytes of data. 64 bytes from fra16s08-in-f196.1e100.net (172.217.16.196): icmp_seq=1 ttl=53 time=16.7 ms 64 bytes from fra16s08-in-f196.1e100.net (172.217.16.196): icmp_seq=2 ttl=53 time=14.3 ms 64 bytes from fra16s08-in-f196.1e100.net (172.217.16.196): icmp_seq=3 ttl=53 time=14.4 ms ^C --- www.google.com ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 5ms rtt min/avg/max/mdev = 14.304/15.130/16.672/1.091 ms
What we see above: We sent 3 packets to a google server and got 3 responses. The packets are numberd with a sequence id, so we would know if there are packets missing in between or if the packets arrived in different order. We also see the time in milliseconds for the round trip. Here about 14ms.
Here the ping also does a reverse lookup
on the IP address. This can be avoided with the -n switch of ping. This should be used of you are cutoff from the network, since then the reverse lookup will not work but you want to use the ping tool to troubleshoot anyways.
Then there is the ttl value: Each time a package is forwarded from one network segment to the next the ttl counter of a package is decreased by one. The packages is sent with an initial value and if it ever gets to zero, then the package is thrown away (and the sender is notified that its packet is thrown away). Most of the time either 64 or 255 is used as a start value. In our case it was most likely 64 that was used by google in its return package. From this we can infer that the distance, measured in the number of networks in between, is abut 12 hops.
If there is package loss
then the quality of the transmission is bad. On a TCP/IP Connection a station is supposed to lower its transmission rate when it encounters packet loss on a transmission the speed of a connection will rapidly drop. For details see: https://en.wikipedia.org/wiki/TCP_congestion_control
The reason for the drop of packages could be some transmission errors, e.g. on a wireless connection, or, most often, if the bandwidth of a link in between is saturated, the router has to drop packages.
It is often useful to send pings with different package sizes and see how they behave. (Sometimes small packages get through while longer ones are dropped).
traceroute
If you want to know which way your packets are taking then you can use traceroute. e.g.:
$ traceroute www.google.com traceroute to www.google.com (172.217.22.68), 30 hops max, 60 byte packets 1 * * * 2 ten2-533-r01interxion.bb.funkfeuer.at (78.41.115.113) 1.758 ms 1.726 ms 1.675 ms 3 144.208.213.177 (144.208.213.177) 2.584 ms 2.552 ms 2.510 ms 4 ae1-0.bbr02.anx84.nue.de.anexia-it.net (144.208.208.137) 14.301 ms 14.281 ms 14.275 ms 5 ae0-0.bbr01.anx84.nue.de.anexia-it.net (144.208.208.139) 14.237 ms 14.217 ms 14.147 ms 6 ae2-0.bbr02.anx25.fra.de.anexia-it.net (144.208.208.141) 14.167 ms 14.047 ms 14.003 ms 7 209.85.149.86 (209.85.149.86) 13.940 ms 13.684 ms 13.611 ms 8 108.170.252.1 (108.170.252.1) 14.202 ms 14.967 ms 14.930 ms 9 72.14.232.35 (72.14.232.35) 14.911 ms 72.14.232.33 (72.14.232.33) 14.863 ms 72.14.232.35 (72.14.232.35) 14.849 ms 10 fra15s17-in-f68.1e100.net (172.217.22.68) 14.833 ms 14.763 ms 13.523 ms
traceroute shows us the path that our packages are traveling. Above we see that google is 10 hops away. Traceroute also users DNS lookup to print names instead of IPs. We can turn this of with the -n switch again. We also see the time that it takes to reach the routers in between. So if a connection does not work, then we say where the issue us. In many cases there are firewalls that prevent us to see the packdets. * * * is shown for this systems.
How does traceroute work? It sends out packages like ping, but it sets a low TTL value so that the packes are thrown away by the routers. The router then informs us. This way we can learn which way outgoing packets are traveling. The TTL starts with 0 and increases by 1 for each router we want to discover. So the next time your internet is not working you can use this to find out if your line is down, your internet provider has a problem or the internet provider of the server you want to reach has issues. Be sure to use the -n option to turn of reverse-DNS lookup.
In today's Internet, package often travel different ways in each direction. Traceroute only shows the outgoing path.
ip, ifconfig
We already learned about ifconfig and ip in the [section]
Those tools can also be used to change the configuration of your network cards. Of course, only the root user is allowed to do that, here are a few examples. To try this out you need to replace the examples with the names of your network card. Beware that you will cut off your network access. To indicate that you need to do this as root I will write # as the prompt symbol insteas of $. The name of my card here is eth7. (Naming the network interfaces eth0, eth1, ... and so on was the original way the kernel used - today's distribution use different naming schemes) If you just want to see all your interfaces run ifconfig or ip link.
If you want a saver interface to play with you can create a dummy interface. E.g. like that:
# ip link add dummy0 type dummy # ip link set up dev dummy0
Below I use eth7 is my example interface.
# ifconfig eth7 10.11.12.13/24
# ifconfig eth7
eth7: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 10.11.12.13 netmask 255.255.255.0 broadcast 10.11.12.255
ether 98:29:a6:2f:4f:3e txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device interrupt 125 base 0x9000
The above example shows how we used the ifconfig tool to set the IP address of eth7 to 10.11.12.13 and we set the network to be a class-C (that is /24 or netmask 255.255.255.0). As you can see: that card is not in use because we do not have any packets counted there.
Here is the same using the more modern ip tool:
# ip addr add dev eth7 10.11.12.13/24
# ip addr list eth7
2: eth7: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc pfifo_fast state DOWN group default qlen 1000
link/ether 98:29:a6:2f:4f:3e brd ff:ff:ff:ff:ff:ff
inet 10.11.12.13/24 scope global eth7
valid_lft forever preferred_lft forever
The ip addr add adds a new address to the interface. If that IP and netmask already exist you will get an error. So you have to either delete it before or use the ip addr replace.
You can add more then one IP with ip addr. You can not do this with ifconfig. What can be done with ifconfig is adding alias interfaces
which are kind of virtual interfaces on the same network card with independent configuration. To add an alias interface you can do this e.g. with:
# ip addr add 10.33.44.1/24 dev eth7 label eth7:1
This would create a virtual interace eth7:1 on the main interface eth7. It is perfectly fine to have more then one IP on an interface. Either in the same network or in a totally different one. You can run completely different network ranges on the same wire - the only downside is that they are not isolated from a security point of view. To do this one can use VLANs.
dhcp with dhcpclient
When you connect a laptop to your network you usually do not have to do any configuration of network settings at all. This is due to a system called DHCP (Dynamic Host Configuration Protocol). Where you have one server on your network that tells new stations on the network which free IP address they are allowed to use and a lot of other network parameter. All the stations need to do is sending specially formated broadcast packages.
This is good and nice for connecting new devices to the network quickly. For servers many companies prefer to set up static address that never change. (You could configure your DHCP server to always give the same address to the machine with the same MAC address but the server then would be still dependent on the dhcp service).
ipup, ipdown, /etc/network/interfaces
All your configuration changes with ip or ifconfig are not permanent! They will be lost when you reboot your machine. So when you want to permanently configure your network you need to write your settings into a configuration file that is used on startup.
Redhat based distributions use configuration files in the directory /etc/sysconfig/network-scripts/ where you have one script for each cards that define IP address and other parameters of the network.
Most other distributions use /etc/network/interfaces where network cards are define. For each card there is a block of settings. E.g.:
$ cat /etc/network/interfaces
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet static
address 10.22.44.42
network 10.22.44.0
netmask 255.255.255.128
broadcast 10.22.44.127
gateway 10.22.44.1
up /etc/myfirewall.sh
auto eth1
iface inet dhcp
In the above example 3 interfaces are define: lo, eth0 and eth1. eth0 is with a static configuration while eth1 will ask a DHCP server. Notice the up keyword: After that keyword you can write a command or a script that it is executed when the interface goes up. E.g. you could write a script that installs a firewall.
Once you have a configuration file like above you can take interface up and down with the comands:
ifdown eth1 ifup eth1
Here you do not need to specify anything but the name of the interface, the rest comes from the /etc/network/interfaces configuration file.
netstat and ss
One tool that can display a lot of network settings if run with different options is netstat. We will not cover it in detail now. Like ifconfig is replaced with ip, netstat is now going to be replaced with the ss tool. One useful thing about netstat and ss is that they can display existing network connections from and to you machine and also list which server ports are active on your system. We will learn about this later.
NetworkManager for GUI programs
When you use your laptop with a GUI environment like GNOME or KDE, you will see some applets that allow you to set up your WiFi and other network options. These programs do not directly use the network tools but connect to a program called NetworkManager
. This is useful on laptops and to some degree also on desktop-PCs but should not be used on servers. For servers it is better to directly configure your network with the network tools. There is a useful command line tool that also talks to the NetworkManager. (E.g. if you are using a laptop but still want to automate some network things.) The tool is nmcli.
nmcli without options lists your network interfaces and tells you which of them are managed by NetworkManger.
Looking at your network traffic with tcpdump
Sometimes you want to see which packets are on the network. The tool to use there is tcpdump. Unlike what the name suggests, tcpdump does not only tell you about TCP traffic but any kind of ethernet traffic. It knows about a lot of network protocols and can decode them for you so that you see what is going on.
Here is an example of using tcpdump:
# tcpdump -ni eth0 not port 22
13:40:09.295326 IP 213.235.242.217.4569 >
193.238.157.20.4569: UDP, length 12
13:40:09.322544 IP 141.89.64.1.27650 >
193.238.157.20.53: 16832% [1au] AAAA? dns.mond.at. (40)
13:40:09.322785 IP 193.238.157.20.53 >
141.89.64.1.27650: 16832* 0/1/1 (88)
13:40:09.483043 arp who-has 192.168.30.32
(ff:ff:ff:ff:ff:ff) tell 192.168.30.32
13:40:09.516130 IP 194.168.8.110.32771 >
193.238.157.20.53: 57265 MX? area23.mond.at. (32)
The -n flag tells tcpdump that we do not want name lookup. The -i tells it on which interface we want to listen. Here interface eth0. After that we can add some filter expression that limits the output to certain types of packages. Here we say everything except packages that use port 22. Port 22 is used for ssh connections. This is useful, because if we are connected via ssh and doing our tcpudmp on the port that is also used for the connection then every package that goes on the wire creates an output over our ssh connection, which in turn would generate a package. The result would be a fast scrolling screen were we do not see what we want but only create artificial traffic.
In the example above we see some packets and also decoded DNS requests and an ARP package.
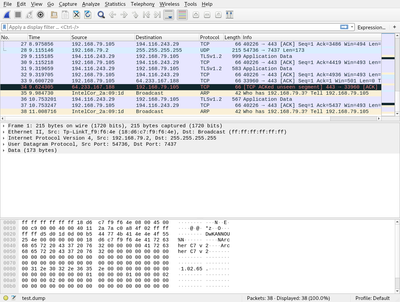
You can also write the captured packages to a file (option -w ) and later analyze it: Either be reading it with tcpdump again or opening the dump file with a graphical tool like wireshark.
Exercises
- Lookup the IP address of some server that you often use.
- Try to create some shortcut host names for machines on your network in the /etc/hosts file
- Use ping to a few different machines. What does the output tell you?
- Use traceroute to the same machines.
- View the network configuration on your machine. Try to create a dummy0 interface or an alias interface and play around with the settings there.
- If you are on a network with DHCP: try to run dhcpclient -v on the interface.
- If you have a laptop where NetworkManager is running: try out nmcli.
- Use tcpdump to look at some network traffic. Respect the privacy of other uses.